
Remember the days when putting up a big, digital firewall felt like installing a castle moat? Fast forward to today, and that moat isn’t just outdated—it’s basically a kiddie pool. As cloud environments expand across regions, devices, and even time zones, perimeter-based defenses just don’t cut it anymore.
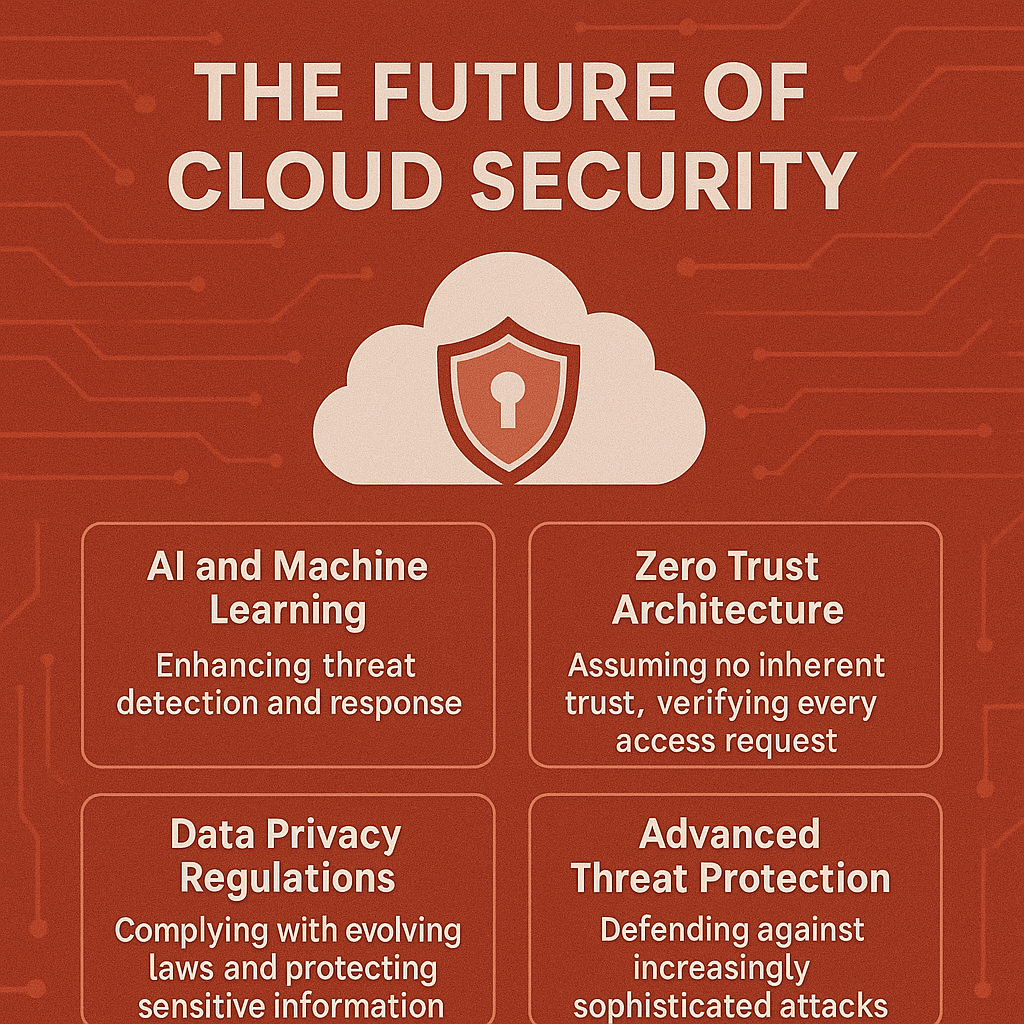
Instead, cloud security is morphing into something much smarter—more like an invisible, adaptive system that constantly watches, learns, and adjusts. We’re seeing the rise of AI-driven detection, Zero Trust frameworks, decentralized identity, and edge computing—all reshaping how we think about protection in the cloud.
This blog digs into the future of cloud security. You’ll learn how traditional models are evolving, why context-aware security matters, and what technologies you should actually care about (hint: it’s not just more tools). From predictive threat intelligence to passwordless authentication, the next generation of cloud security is all about smarts, not just strength.
“Security used to mean building taller walls. Now, it’s about smarter paths.” — Chris Hughes, CISO & Cloud Strategist
Whether you’re managing a team, a platform, or just trying to not get hacked on a Tuesday, this blog breaks down what’s coming—and how you can be ready. And we promise: no fear-mongering. Just practical, useful insights (with a few jokes to keep it human).
Let’s say you’ve just finished reading this blog and think, “Okay, I need to step up our cloud security game.” Then the next question hits: Where do I even find the right people for this stuff?
That’s where Proso steps in.
Proso is a next-gen talent marketplace built for businesses that need tech expertise on demand—especially in areas like cloud security, compliance, infrastructure, and automation. Whether you're a scaling SaaS company or a healthcare platform bound by HIPAA, Proso connects you with vetted experts who understand your stack and can implement complex solutions fast.
Here’s how it plays out in real life:
With Proso, you skip the fluff. Just post what you need, get matched with the right tech professionals, review their track records, and get started. No agencies. No ghosting. No overpaying for bloated teams.
“With Proso, I felt like I had an entire security ops team—without hiring one.”
— Daniel K., CTO at a mid-sized SaaS firm
So if upgrading your cloud security feels intimidating, don’t sweat it. Proso makes it doable—and fast.
Cloud security is no longer about having the strongest walls—it’s about having the smartest systems. As we move toward decentralized models, AI-powered defenses, and user-centric access, the future looks less like a fortress and more like an intelligent mesh.
We’re entering an era where security is invisible, adaptive, and automated. No more remembering 30 passwords or relying on static rules. With context-aware systems and smart authentication, your cloud can be safer without being a pain.
Here’s what’s next:
If you’re reading this and thinking, “Where do I even start?”—start small. Audit your current setup. Look at your weakest link. Then evolve piece by piece.
📌 This blog will be updated regularly with new trends, tools, and examples—so bookmark it. Stay tuned for interviews with cloud security leaders and breakdowns of real breach postmortems (the juicy kind).
👉 Have your own story to share? Drop us a line—we’re building a future-proof security community one reader at a time.
Until next time, stay smart, stay cloud-ready, and maybe don’t reuse your Netflix password.
